Insider Threat Mitigation
“The penny drops when you realise that planning for Insider Threat is partly questioning the loyalty of people you work with every day, people you know well”
by Alex Bomberg | 1st Jun 2019

Insider Threat Data Breaches, Are You Prepared?
From December 2018 until the end of April 2019, our sister company International Intelligence Limited carried out an investigation into an Unauthorised Disclosure for a UK Government Department, the investigation was extensive, and the findings thought provoking. In organisations with little security culture, Insider Threat is a troublesome area and one that requires a mature, delicate approach, where a culture change and accountability does not apportion blame.
Information has a different value to different people, to someone who has daily access to sensitive information, the sensitivity can often diminish over time, this coupled with weak or non-existent policies and data control can be a recipe for disaster, if there is no proper control in place.
Of course, it goes without saying even with robust contracts and Non-Disclosure Agreements or professional codes of conduct, such as the Civil Service Code, unauthorised disclosures and breaches can still take place. A recent example of this is the UK’s National Security Council breach over discussions on the Chinese firm Huawei and the UK’s G5 Network. The Crown Prosecutor deemed that the breach was not going to be investigated as a breach under the UK’s Official Secrets Act.
Jeremy Wright, Culture Secretary, told the House of Commons that “National Security Council discussions should be confidential.” ... Peter Ricketts, the UK's first National Security Adviser, said: “I assume this leak is a breach of the Official Secrets Act because everyone around the table would have signed it.”
The above example raises more questions:
- Should that be an end to the matter or should an external investigation have taken place?
- What effect does inaction have on public opinion?
- What else may have been leaked?
- How is it possible to learn and mitigate without proper investigation and knowing the facts?
July 2019 saw the British Ambassador to the United States Sir Kim Darroch resign, after emails critical of President Trump's administration, calling the President "clumsy and inept", were leaked. The incident has caused a great deal of tension between the two countries. This 'Kim Darroch incident' is a prime example of Insider Threat (Unauthorised Disclosure), where someone has physically leaked information. The motivations may of course never be known, even after investigation.
Dealing with Insider Threats in any organisation is difficult, and more so within Government Departments, where the trust is highlighted by the Official Secrets act and within the Civil Service Code.
It is not easy for those Civil Servants managing Government Departments of any size, they have to make difficult calls on a daily basis. The loss of public confidence in a Government Department due to a Data Breach is a real concern and a breach at this level if left unmanaged will do nothing other than to cause damage further down the line.
Commercial organisations value their information differently, being more attuned to the likes of Intellectual Property and of course profit is a good motivation to protect reputation.
Cyber Threat vs Physical Threat
No amount of spending on Cyber Security would have stopped the above breach taking place. Organisations cannot be blinkered into thinking that Cyber Security is the answer to everything, it's most definitely not!
Organisations need to employ security professionals who are multi-disciplined and who have a rounded, holistic view of security. Cyber security is highly important, but not more important than physical security – but raising this at board level might raise a few eyebrows!
Managing the people within an organisation and empowering them to handle, respect and take ownership for the information that they deal with daily is a real challenge, but with the right leadership, policies and training, the appetite for secure practices will develop and cultures will change.
Managing Insider Threat
Managing for “Insider threat” or its mear mention is not going to motivate your workforce, casting suspicion on an otherwise loyal workforce does not seem a great place to start when it comes to security, but your staff are in most respects your first and last line of defence.
We should be clear that not all Insider Threat is with malicious intent. Employees may inadvertently cause a Data Breach or Unauthorised Disclosure through lack of training or lack of understanding, this can be then categorised at “Employee negligence or error”; the real “point of failure” being training and management of that individual.
“Employee negligence or error” breaches are quite common and can happen in fast growing organisations or equally in start-ups, or where people move laterally within an organisation. An example of this could be a poorly introduced and managed Bring Your Own Device (BYOD) Policy. The points of failure being the lack of a substantive policy, lack of training in understanding cyber threats and a casual click on a link, introducing malware to a Device. It really is that simple.
US based cyber firm Varonis produced a recent Data Breach Report that highlighted a shocking trend, and that is that the amount of data that is being handled is getting out of control for some firms and that is leaving them exposed.
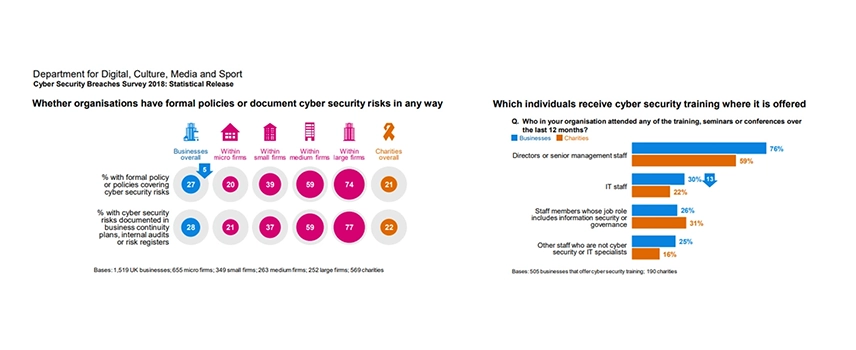
This latest 2019 report gave some interesting statistics taken from firms around the globe.
- Every employee can access a whopping 17 million files.
- 53% of companies had at least 1,000 sensitive files open to all employees.
- 22% of all folders were accessible, on average, to every employee.
- 38% of users had passwords that never expire, up from 10% last year.
- 40% of companies had over 1,000 enabled, but stale, “ghost” users.
- Retail organizations had the lowest number of exposed, sensitive files and seemed to do the best job of protecting their data overall.
- Financial services firms found the most exposed, sensitive files overall.
- Healthcare, pharmaceutical and biotech firms found the most exposed, sensitive files in each terabyte that they analyzed.
Understanding Motivations of Insider Threat
Before looking at steps to mitigate Insider Threat, it would be useful to try to better understand the motives of Insider Threat, and for this, we can draw upon the cold war acronym MICE: Money, Ideology, Compromise or Coercion, Ego or Extortion.
The MICE acronym is self-explanatory and useful in planning a defence. Perhaps the hardest pills for an organisation to swallow and that are the most difficult to combat against is someone acting under the auspices of Ideology or Ego. Damaging the organisation because of their beliefs’, be they political, religious or just that their own personal view differs greatly from the organisation, motivating them to act maliciously will have a direct impact on morale.
It is hard enough for an organisation to recover from an Insider Threat incident and maintaining staff morale has to be a high priority.

Five Steps to Mitigating Insider Threat:
1. Insider Threat ProgramThe number one tip to combatting the Insider Threat is having an “Insider Threat Program” that you can draw upon, this will include by design Incident Response.
Incident Response is the agreed “actions on” discovering a Data Breach or Unauthorised Disclosure.
The idea of an “Insider Threat Program” was conceived by the US Government in response to the Bradley Manning breach. The concept of an Insider Threat Program is entirely scalable to businesses of all sizes, organisations just need the will and resources.
An Insider Threat Program will identify via an Insider Threat Asset Register, the Intellectual Property, functions, data etc. that are likely to be classes as high risk, prioritising them in order of importance to your organisation.
Any such register should list stakeholders and owners of the data and list access rights. It is also an opportunity to review what data a firm might want to monitor access of. There are some very professional products on the market that allow the monitoring and forensics of data, one such firm offering products in the space is US based Varonis. We recommend the use of their products, as the allow for threat models that look for unusual patterns of access using User Behaviour Analytics. More information on Varonis and their products can be found on their website, here: Varonis
An Insider Threat Program can be as simple or as complex as an organisation wishes to make it, based on that organisation’s appetite for security vs risk profile.
2. PoliciesThese are the background of any defence against Data Breaches. A well written and understood policies will greatly mitigate the risk of a Data Breach or Unauthorised Disclosure. Of course, we are not talking about a single policy, but rather a group of policies, from your IT Security policy, through to your Social Media policy, they all play a small part in good security practices.
One policy worthy of a special mention is a Whistleblowing policy. A Whistleblowing policy, if you do not have one, can be tour fist line of defence and it will encourage and enable employees to voice their concerns about possible/suspected misconduct carried out by other employees or contactors.
This policy will outline how the information is dealt with, the anonymity of the Whistleblower, and how they are to be treated by the organisation in relation to feedback etc.
“All good security policies start with a difficult conversation” - Alex Bomberg, Group CEO, Intelligent (UK Holdings) Limited
It is good practice to have a working group on policies that will refer to other policies maybe outside the authors area of expertise. One example of this is a BYOD policy that needs input from Human Resources specialists with respect to possible breaches of personal privacy – ownership of data on such devices being also a legal minefield.
3. TrainingWhatever policies and procedures your organisation have, training and open discussion will serve to educate the workforce, drill and test good practices.
The outcome of professional training is rarely wasted. Should your organisation ever be subject to an external investigation, training records are important, they are the difference between poor and malpractice, negligence and wilful neglect.
4. AuditingAuditing is not just about “Who has access to what and why?” It's also about understanding what sensitive data is dealt with: has this changed over time, have any changes to internal policies or externally, changes to laws had an impact on how the organisation might be exposed?
The justification of access to sensitive data on a “business case” basis and auditing both Access Rights and Delegated Access Rights should be the main focus of any audit. This would mitigate people having needless access to data and thus lower risks.
Annual auditing of policies is vital to ensure that they remain up to date and lawful. Further to this, if they intern refer to other policies, that these polices still exist.
5. LeaversIt is never easy dealing with leavers as it directly affects the morale of the workforce, whatever the reason for someone leaving, besides retirement. If you have normal situation where a notice period applies, then of course it is easier, to debrief leavers with a leavers interview and access rights can be reviewed and restricted as required.
Of course, a situation where an employee is dismissed for whatever reason will heighten the risk of that individual setting out to cause damage to your organisation, and for that reason it is worth “getting legal” as early as possible with a “Settlement Agreement”.
“A Settlement Agreement is a legally binding contract between employer and employee which settles claims that the employee may have against their employ” – but, over and above this, it gives the employer the chance to lock the employee into a well understood legal position.
Unauthorised Disclosure and Data Breach Investigations
International Intelligence Limited provides an in-depth Data Breach investigation service that encompasses all aspects of the breach, from circumstances surrounding the breach, to the policies and procedures in use. It is rare for a Data Breach to have a single point of failure, our team of investigators works extremely closely with the client to ensure that the client does all that it can to mitigate any damage to the organisation, that the situation is controlled, whilst causing as minimum disruption to daily operations.
Whatever course of action an organisation takes, its integrity will be measured by public opinion, so, swift decisive action is required. If you require further information, please see: Data Breach Investigations.